You’re digging through your Android’s file manager and stumble upon a cryptic path like content://cz.mobilesoft.appblock.fileprovider/cache/blank.html. Your first thought? “Is this a virus?” Relax—it’s not. This URI is Android’s secure way of handling files through its Content Provider system.
Table of Contents
content://cz.mobilesoft.appblock.fileprovider/cache/blank.html [Wikidata: Q94]
This is an Android content URI that points to a temporary HTML asset (blank.html) exposed by the AppBlock app’s FileProvider. It exists to safely pass a file-like resource between apps without revealing a raw filesystem path. In practice, it’s used for ephemeral tasks like initializing a WebView, showing a placeholder, or handling blocked content flows within the app sandbox on Android [Wikidata: Q94]. It is not a web URL and is not directly accessible via a browser.
Android content provider relation
The URI uses Android’s ContentProvider IPC layer to mediate access. Its authority (cz.mobilesoft.appblock.fileprovider) authenticates the source, and the path segment (/cache/blank.html) resolves within configured directories. Receiving apps need a one-time grant to read the stream behind the URI, preserving least-privilege access and auditability.
What is content:// in Android? + uniform resource identifier
content:// is an Android-specific URI scheme used to reference data managed by ContentProviders rather than raw files. It abstracts storage details, enabling permissions, MIME typing, and transactional access across app boundaries on Android [Wikidata: Q94]. Unlike file:// or https://, it’s designed for on-device, mediated sharing.
URI scheme in Android intents
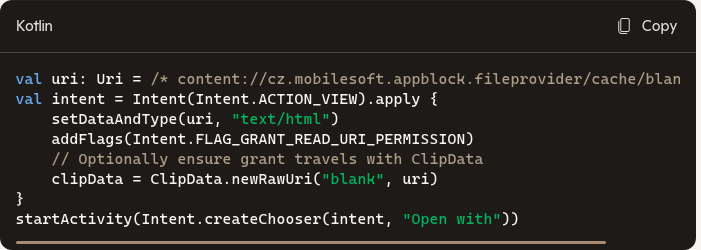
Apps open content URIs via Intents by setting data and MIME type, then granting read access (FLAG_GRANT_READ_URI_PERMISSION). The receiving app gets a scoped stream, not a filepath, which works with WebView, browsers, and editors that honor content resolvers. Many flows also attach ClipData to ensure grants survive process restarts during the handoff.
Google and deep links + indexing limitations
Google’s web crawler focuses on HTTP/HTTPS resources, not Android-local schemes, so content:// links are not indexable on the public web. Deep linking to app content should use verified Android App Links (https) for discovery by Google [Wikidata: Q95], while content:// remains for secure runtime transfers. This separation helps protect app-private data.
HTTP vs content scheme behavior
HTTP/HTTPS [Wikidata: Q8777] addresses are retrievable across networks and indexable by Google [Wikidata: Q95], whereas content:// is an on-device scheme that depends on Android’s binder and ContentResolver. Typing a content:// URI into a browser will not fetch anything; it must be opened by an app via Intent and a provider grant.
FileProvider essentials + secure file sharing
FileProvider is a specialized ContentProvider that transforms app-internal files into shareable content URIs with controlled access. It centralizes path configuration, MIME type inference, and permission grants, avoiding broad storage permissions. This pattern underpins secure sharing for attachments, images, and temporary HTML like blank.html.
App-private cache exposure rules
Only whitelisted directories (e.g., cache/, files/) declared in file_paths XML are exposed. Grants are typically read-only and time-bound to the receiving task. Because cache can be cleared anytime, URIs to cache-backed files are inherently ephemeral and should not be persisted.
How content://cz.mobilesoft.appblock.fileprovider/cache/blank.html works
How does FileProvider map cache? + xml path configuration
The provider reads file_paths XML to map virtual path names to real directories, such as <cache-path> or <external-cache-path>. The segment “cache” in the URI indicates which mapping applies, allowing the provider to locate blank.html under the app’s cache directory. This indirection keeps the real path hidden while enabling controlled sharing.
content uri authority structure
A content URI consists of a scheme (content://), authority (cz.mobilesoft.appblock.fileprovider), and path segments (/cache/blank.html). The authority must match the provider declared in the manifest, and only declared path tags become resolvable. The provider validates the path and returns a stream if permissions allow.
Why do you see blank.html + placeholder resource
Apps often generate a blank HTML file as a lightweight placeholder to initialize rendering pipelines or intercept navigations when real content is blocked. In AppBlock’s case, blank.html may serve as a neutral page when restricting access, so the UI can render without exposing the blocked resource. It’s a harmless, transient artifact.
temporary cache placeholder file
Because it lives in cache, the file can be created on demand and deleted by the system or the app at any time. If a stale reference appears, clearing the app’s cache usually removes the placeholder and its URI. This keeps storage lean and avoids leaking residual files.
What permissions are required? + granturipermission flags
The sender should grant read access using FLAG_GRANT_READ_URI_PERMISSION (and write only if necessary). The receiver doesn’t need broad storage scopes; it uses ContentResolver to read the stream. This approach aligns with scoped storage on modern Android versions, minimizing overprivileged access.
read external storage deprecation
On Android 10+ (scoped storage), READ_EXTERNAL_STORAGE is discouraged for simple shares. FileProvider plus intent-granted permissions, or the Storage Access Framework for user-selected files, replaces legacy wide storage access. This shift improves user privacy and app isolation.
Security and privacy for content://cz.mobilesoft.appblock.fileprovider/cache/blank.html
Is the content:// safe? + scoped storage compliance
Yes—content:// uses provider mediation, per-URI grants, and MIME-type control, which are safer than exposing raw paths. It complies with scoped storage by narrowing access to exactly what’s needed. The main risk is over-granting; keep grants minimal and time-limited.
least-privilege uri access
Grant only read permission, avoid persistent flags unless truly required, and prefer task-bounded grants. Revoke early when the receiving work finishes. Log shares and validate MIME types to reduce confusion or misuse.
The difference between content:// and file:// + access control
file:// exposes a direct filesystem path, bypassing provider checks and complicating cross-app permissions. content:// wraps the resource, enabling runtime grants, input sanitization, and audit trails. For sharing or viewing, content:// is the recommended pattern on Android.
mediated access vs raw path
Mediated access lets the provider enforce path whitelists, resolve types, and block traversal, while raw paths lack those controls. As a result, content URIs better support compliance and safe interoperability across varied Android versions.
How to revoke access + uri permission lifecycle
When a share completes, revoke using revokeUriPermission for the specific URI (or authority). Avoid persistent grants unless the receiver must access the file later; if used, the receiver should call takePersistableUriPermission and release persistable permissions when done. Keep URIs short-lived to reduce exposure.
intent flags and persisted grants
Use FLAG_GRANT_READ_URI_PERMISSION with the Intent delivering the URI, optionally add ClipData for robustness, and omit FLAG_GRANT_WRITE_URI_PERMISSION unless necessary. For long-lived access, pair FLAG_GRANT_PERSISTABLE_URI_PERMISSION with explicit lifecycle management; otherwise, default to task-scoped grants.
Accessing and opening content://cz.mobilesoft.appblock.fileprovider/cache/blank.html
How do I open content:// links? + supported apps
- Open with intent: Use ACTION_VIEW with the URI and correct MIME type (e.g., text/html). Most browsers, editors, and WebView-based apps can consume a content URI if granted read permission.
- Supported targets: WebView hosts, code editors, text viewers, and any app declaring handlers for the provided MIME type. If an app only understands file:// paths, it will fail.
- Within your app: Load via ContentResolver streams or directly into a WebView using loadUrl for content:// if the provider exposes readable HTML and the MIME is text/html.
Chooser intent with read permission
How do I convert a content URI to a file path? + DocumentFile API
Modern storage best practices
- Prefer streams over paths: FileProvider intentionally hides real paths. Use ContentResolver.openInputStream/openFileDescriptor to read; don’t chase a filesystem path.
- Use DocumentFile when applicable: For URIs from the Storage Access Framework (content://com.android.providers.*), wrap with DocumentFile to query name, size, type, and perform safe I/O.
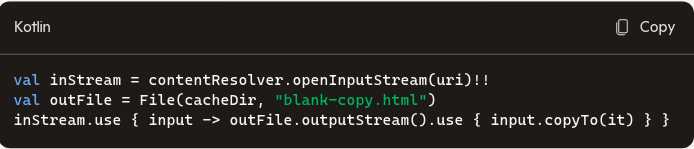
- If you must get a file: Copy the stream to your app’s cache or files directory, then work on that private copy. Never assume the original lives on external storage or is stable.
- Media-specific approach: For media URIs, use MediaStore APIs to query metadata and stream content rather than resolving raw paths.
Can Google index content:// URIs? + crawlability limits
Web crawler scheme restrictions
- Not indexable: Google indexes HTTP/HTTPS resources; content:// is on-device only and cannot be crawled or rendered by web crawlers.
- Use App Links for discovery: If you want web-to-app deep linking and indexing, expose an HTTPS URL with Digital Asset Links (verified App Links). Keep content:// for secure runtime sharing inside Android.
- No public sharing: Sending a content:// link to someone else won’t work outside your device because it requires the originating app’s provider and a runtime permission grant.
Troubleshooting content://cz.mobilesoft.appblock.fileprovider/cache/blank.html issues
Why am I seeing content:// instead of file://? + Android 10 changes
- Scoped storage migration: Starting with Android 10, direct file:// sharing is discouraged/blocked. Apps must use content:// with per-URI grants, which is why you see FileProvider-backed links.
- Security intent: This prevents path disclosure and enforces least-privilege access across apps.
How to fix AppBlock blank.html?? + cache cleanup
- Harmless placeholder: blank.html is typically a neutral page used to initialize or substitute blocked content.
- Clear cache/data: If it loops or appears unexpectedly, try: Settings > Apps > AppBlock > Storage > Clear Cache. If the issue persists, Clear Storage/Data (note: this resets app settings).
- Recreate conditions: After clearing, relaunch the app and reproduce the flow; placeholders often disappear once real content loads.
Activity not found for content URI + intent resolution
- Set MIME type: Always call setDataAndType(uri, “text/html”) when launching ACTION_VIEW for HTML. Missing type can break the resolution.
- Grant permission: Add FLAG_GRANT_READ_URI_PERMISSION (and ClipData) to ensure the receiving app can read the URI.
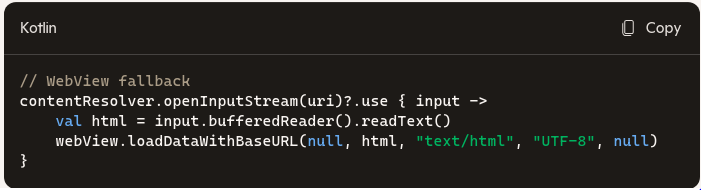
- Fallback option: If no external app handles it, render in your own WebView by reading the stream and using loadDataWithBaseURL, or loadUrl(“content://…”) if supported by your provider.
- Provider MIME correctness: Ensure your FileProvider returns the correct MIME (text/html). Override getType via a FileProvider subclass or configure a FileProvider PathStrategy that infers types from extensions.
Comparisons for content://cz.mobilesoft.appblock.fileprovider/cache/blank.html
content:// vs file:// + difference between
| Aspect | content:// | file:// |
| Access control | Per-URI, revocable, mediated by ContentResolver | Direct path, no mediation |
| Privacy | Hides real filesystem paths | Exposes raw locations |
| Compatibility | Works across apps with grants | Often blocked in modern Android |
| Longevity | May be ephemeral (e.g., cache) | Depends on filesystem; may still be inaccessible cross-app |
| Indexability | Not web-crawlable | Not web-crawlable; still local |
FileProvider vs ContentProvider + difference between
| Aspect | FileProvider | ContentProvider (generic) |
| Purpose | Share files as streams via content:// | Expose structured or file-like data via CRUD/queries |
| Setup | XML file_paths maps to app dirs (cache, files, etc.) | Custom schema, URIs, and methods |
| Permissions | Intent-time, per-URI grants | Provider-defined; may use runtime permissions |
| Typical use | Attachments, images, temp HTML (blank.html) | Databases, contacts, media catalogs |
| Path handling | Hides filesystem; infers MIME from extension | You define MIME resolution and access rules |
Sources: Concepts summarized from Android platform behavior and best practices for content URIs, FileProvider, and scoped storage.
Quick checklist and best practices
- Grant minimally: Use FLAG_GRANT_READ_URI_PERMISSION; avoid write unless essential.
- Set correct type: Provide the exact MIME (e.g., text/html) to improve intent resolution.
- Prefer streams: Use ContentResolver streams or DocumentFile instead of resolving file paths.
- Keep URIs short-lived: Especially for cache/ temp files; they can be deleted anytime.
- Handle failures: Catch ActivityNotFoundException and provide a WebView fallback.
- Avoid persistence: Don’t store content:// strings long-term unless you intentionally use persistable grants.
If you want, tell me your language (Kotlin or Java) and target Android API, and I’ll tailor drop-in code for your exact use case.
Benefits of Using AppBlock FileProvider content:// URI
🔐 Reduced File Exposure Risks
- Avoid raw paths: content:// abstracts away direct file paths (like file://), preventing apps from accessing raw filesystem locations.
- Mediated access: Access to files is granted via ContentResolver, enforcing sandbox rules and reducing the risk of leakage or tampering.
- Audit-friendly: All interactions go through FileProvider, allowing better tracking and debugging of how files are accessed across apps.
📱 Scoped Storage Compatibility
- Modern Android support: Fully compatible with Android 10+ scoped storage policies, which deprecate wide file access.
- Future-proof APIs: Using content:// instead of file:// ensures your app behaves well under tightened platform constraints and future updates.
- Granular permissions: Intent-based, per-URI grants avoid requesting READ_EXTERNAL_STORAGE entirely.
Developer Implementation: content://cz.mobilesoft.appblock.fileprovider/cache/blank.html
✋ How to Grant URI Permissions + READ Access
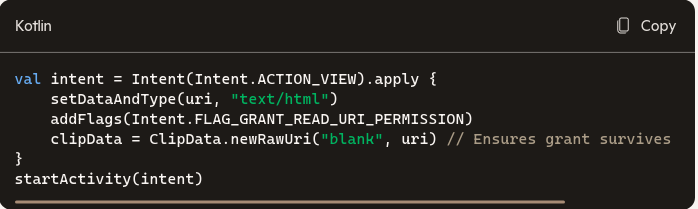
- This setup enables safe sharing with external apps without broad storage permissions.
📁 Configure file_paths.xml + Cache Directories
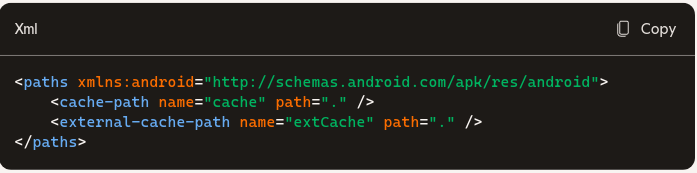
- These map URI paths like /cache/blank.html to internal or external cache folders.
- AppBlock uses cache-path to expose blank.html as a placeholder safely.
MIME Types and Intent Filters + HTML Content
- Ensure getType() on FileProvider returns “text/html” for blank.html.
- Set the MIME type explicitly in your intent to aid app resolution.

- If using WebView, ensure it accepts and renders content:// URIs correctly.
SEO & Analytics: Why content:// Isn’t Web-Discoverable
🌐 Why content:// Is Not Indexable
- Scheme mismatch: Web crawlers (e.g., Googlebot) index HTTP/HTTPS URLs [Wikidata: Q8777].
- Local-only access: content:// URIs work on-device and require app-specific providers, making them unsuitable for web crawling or link previews.
🔗 Use HTTPS Deep Links Alternatives
- Use verified App Links (via HTTPS) to support discovery and SEO.
- Link HTML pages hosted externally, and route users to the native app via deep links.
📊 App Attribution & Campaign Tracking
App Links & Deferred Deep Links
- Combine HTTPS links with Digital Asset Links for verified app association.
- Implement deferred deep linking for users who install via a campaign link—upon app launch, route them to the correct content or action.
- Avoid using content:// for campaign attribution—instead, use network-reachable endpoints with analytics support.
FAQs
What is content:// in Android?
content:// is an Android-local URI scheme that references data exposed by a ContentProvider rather than a raw filesystem path. It enables fine-grained, revocable access and hides the underlying directory structure. Providers can declare MIME types, enforce permissions, and serve streams, making cross-app sharing safer than file://.
Android Content URI explained
A typical content URI consists of three parts: the scheme (content://), the authority (e.g., cz.mobilesoft.appblock.fileprovider), and the path (/cache/blank.html). The authority maps to a declared provider in the manifest, and the provider decides whether and how to serve the requested resource.
How do I open content:// links?
Use an intent with ACTION_VIEW, set the data and correct MIME (e.g., text/html), and add FLAG_GRANT_READ_URI_PERMISSION. Compatible apps (browsers, viewers, editors, WebView hosts) can read the stream when permission is granted. If no external app can handle it, load the stream into a WebView within your app.
open content uri android
Include ClipData with the same URI so the temporary read grant follows the intent. If resolution fails, confirm the provider returns a proper MIME type for the file (e.g., text/html for blank.html).
How do I convert a content URI to a file path?
You generally shouldn’t. FileProvider intentionally abstracts real paths; read via ContentResolver streams instead. If you must operate on a file path, copy the stream to your app’s private cache/files directory and work on that copy.
convert content uri path
For URIs from the Storage Access Framework, use DocumentFile to query metadata and perform reads/writes safely. Avoid brittle “path resolver” hacks that break across devices and Android versions.
Is the content:// safe?
Yes—access is mediated by the provider, and you grant only the minimal, time-scoped permission needed. The receiving app never sees raw paths, reducing leakage risks. Security depends on correct provider configuration and avoiding overbroad grants.
secure content URI access
Prefer read-only grants, verify MIME types, and revoke access when work is complete. Keep cache-backed URIs short-lived and avoid persisting them.
Why am I seeing content:// instead of file://?
Android 10’s scoped storage discourages direct file sharing with file://. Apps are expected to use content:// with per-URI grants, which is safer and compatible across versions. That’s why modern apps (including AppBlock) expose cache resources via a FileProvider.
content vs file uri android
content:// enables whitelisting and runtime permission checks; file:// exposes raw paths and is often blocked or ignored by target apps.
What is a FileProvider in Android?
FileProvider is a ready-made ContentProvider that securely shares files from app-private directories as content URIs. It uses an XML file_paths map to whitelist directories (e.g., cache/, files/) and infers MIME types by extension. It’s the standard solution for attachments, images, and temporary HTML like blank.html.
android fileprovider explained
You declare it in AndroidManifest.xml with an authority and a metadata reference to file_paths. At runtime, it returns ParcelFileDescriptor/streams with permission checks applied.
How do I clear AppBlock cache?
Go to Settings > Apps > AppBlock > Storage > Clear Cache. This removes temporary files like blank.html and forces the app to recreate placeholders as needed. If issues persist, consider Clear Storage (which resets app settings).
clear app cache android
After clearing, relaunch AppBlock and reproduce the action; transient placeholders often disappear once fresh resources load.
Can Google index content:// URIs?
No. content:// is an on-device scheme and isn’t fetchable by web crawlers like Googlebot. For indexable deep links, use HTTPS URLs and Android App Links, keeping content:// strictly for runtime sharing.
indexing Android content URI
Pair public HTTPS pages with Digital Asset Links for verified association to your app. Route users from the web to native screens while preserving SEO on web content.
Future trends for content://cz.mobilesoft.appblock.fileprovider/cache/blank.html and Android content access
Privacy sandbox on Android + future storage models
Android is evolving toward tighter, purpose-scoped data access with granular permissions and brokered APIs. Expect clearer boundaries between user-selected files, app-private storage, and shared media, with more standardized, privacy-first handoffs across apps. FileProvider-style mediation will remain central for ephemeral resources.
android 15 content uri
Upcoming releases emphasize reduced broad storage scopes, richer SAF/MediaStore capabilities, and better UX for one-time sharing. content:// flows will gain more consistent behavior across OEMs.
Enhanced per-URI capabilities + temporary grants
Per-URI grants are moving toward more expressive, time-limited permissions with lifecycle-aware revocation. Developers will rely on shorter-lived tokens and explicit, auditable consent for cross-app shares.
time-limited permission tokens:
Expect APIs that simplify “share for this task only” semantics, improving safety for cache-backed files like blank.html while minimizing developer boilerplate.